Hackers With Examples
List of security hacking incidents wikipedia.
What Is A Hacker Definition Overview Video Lesson
This lesson describes what a hacker is. although we associate a hacker with an individual hacking a. As an example, see: emotet. in another example, windows users are reportedly the target of a wide-spread cybercriminal effort offering remote access to it . Top 10 most famous hackers we present the ten most famous hackers. the former self-styled 'hacker poster-boy': kevin mitnick. 5:18pm gmt 27 nov 2009. 1. kevin mitnick. probably the most famous. The three types of hackers are the white hat hacker, the grey hat hacker, and the black hat hacker. each type of hacker hacks for a different reason, a cause, or both. all have the required skills.
For example, if the source of a river is poisoned, it will hit the entire stretch of animals during summer. in the same way, hackers target the most accessed physical location to attack the victim. Super hacker george hotz: i can make your hackers with examples car drive itself for under $1,000 duration: 35:54. reasontv 2,020,925 views.
Examples of hacking techniques; how to protect yourself against hacking. if you're not careful, hackers can access your computer . Examples of hacking techniques; how to protect yourself against hacking. if you're not careful, hackers can access your computer .
The list of security hacking incidents covers important and noteworthy events in the history of this was an early example of a kind of sportive, but very effective, debugging that was often repeated in the evolution of apl systems. An example of a hacker is someone who loves to play tennis but is not very good at hitting the ball correctly. yourdictionary definition and usage example. For example, when mit students surreptitiously put a fake police car atop the dome on mit's building 10, that was a hack in this sense, and the students involved were therefore hackers. other types of hacking are reality hackers wetware hackers ("hack your brain"), and media hackers ("hack your reputation"). Hackers can launch ddos attacks by infiltrating and leveraging thousands or millions of unsecured devices. they can cripple infrastructure, down networks, and as iot advances into our everyday lives, those attacks may very well put real human lives in jeopardy. and even if hackers don’t outright threaten lives, they can compromise gateways and deeper levels of iot networks in order to reveal.
Computer Hacking Methods Examples Of Cyber Criminals Protect Yourself
Top 10 Grey Hat Hackers 2018 Hacking Grey Hat Hackers Wikitechy

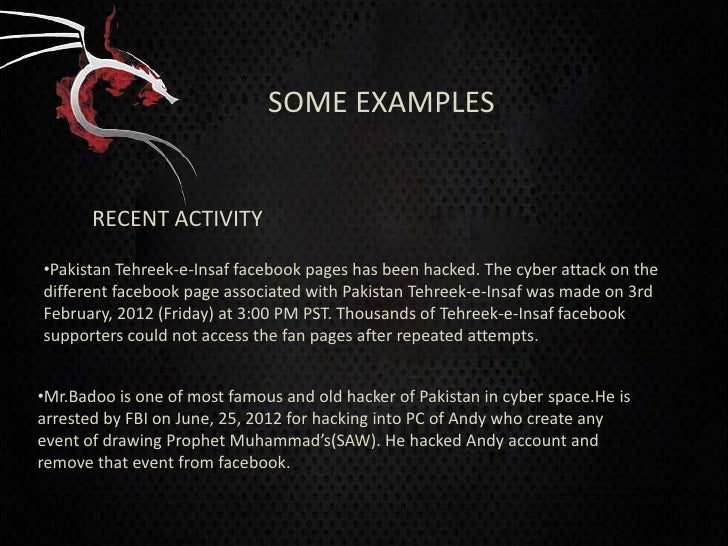
Hackers steal £650 million in world's biggest bank raid investigators uncover what is thought hackers with examples to be the biggest ever cybercrime with more than £650 million going missing from banks around the world. A black hat hacker is a criminal, both morally and legally speaking. black hat hackers would use their skills to break open a digital system to steal or misuse data. such a person would do that for selfish gain. imagine a fully secure bank robbery and they know how to enter the room and steal the money violently or sneakily.
Hoglund is a crucial feature in our list of ethical hackers. some of the areas he is best known for working in include physical memory forensics, attribution of hackers and malware detection. his. Types of hackers: wrap up. i hope this post cleared up your thoughts on the kinds of hackers out there and helped you get a new insight into the hacking world. it is essential to stay aware and vigilant to protect yourself from cyber threats and different types of hackers who may use even the smallest vulnerability in your system against you. . Famous white-hat hackers include the likes of apple's steve wozniak and jeff moss, founder of the defcon and black hat conferences. 1. tim berners-lee. famous not for hacking but inventing the.
27 dec 2019 examples of different types of hacking. hackers use brute force, security exploits, social engineering, and other means to gain access to . These and other symptoms could mean you've been hacked. worse than just a pesky virus, an attack on your system directed by a hacker can be far more . Grey hat hackers that do hacking bit the ethical and non-ethical. these are the persons who knows extraordinary hacking traps and they utilize their abilities to hack up the systems and frameworks of different experts and associations yet in illicit way. they usually break up the security walls of the network for their self-purposes and cause great loss and harm to the authorities.
Internet hacking. it could hurt you computer and even lead to viruses. be carefull for hackers out there. examples: runescape,ourworld,facebook,yahoo and more. The work of famous hackers, both black hat & white hat, has fostered the for example, in 2008 the group took issue with the church of scientology and begin . 1. white hat hacker. first up, we have the perfect type of hacker to break the stereotype. the white hat hacker is hackers with examples a good guy, as ironic as it may sound. white hackers, white hat hackers or ethical hackers are the people who test existing internet infrastructures to research loopholes in the system.
Here are some of the most notorious examples of malware infection, demonstrating the methods and techniques hackers use to penetrate systems. these security breaches have cost computer users inestimable amounts of time, frustration, and money. Dec 27, 2019 examples of different types of hacking. hackers use brute force, security exploits, social engineering, and other means to gain access to . Black hat hackers form the stereotypical, illegal hacking groups often portrayed in popular culture, and are the epitome of all that the public fears in a computer criminal. black hat hackers break into secure networks to destroy data or make the network unusable for those who are authorized to use the network. a black-hat is a term in computing for someone who compromises the security of a.
Komentar
Posting Komentar